Prevent DDoS Attacks with Edgio
We are committed to our clients’ success in everything we do. That’s why we are not willing to compromise on quality or service. Our Edge Security Platform is no exception. See how this dynamic platform will help you improve application resilience and uptime while building a sustainable strategy for years to come:
- Comprehensive Protection offers a layered security approach that addresses Distributed Denial-of-Service (DDoS) attacks.
- Scalable Infrastructure can handle massive traffic spikes and mitigate large-scale DDoS attacks.
- Seamless Integration integrates with existing IT infrastructure, enhancing security without disrupting operational workflows.
- Customizable Solutions are tailored to meet specific organizational needs, ensuring that all aspects of DDoS risks are covered.
Protecting your business now could save you millions of dollars later. Let Edgio in to bring you increased revenue, unparalleled service…and peace of mind.
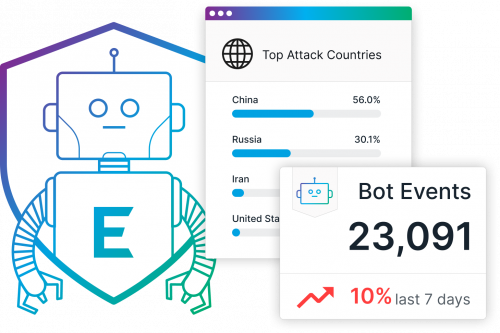
The Exponential Threat of a DDoS Attack
Your business is going along seemingly well and then like a traffic jam, the flow of business all comes to a halt. Sound familiar? If you have ever experienced a Distributed Denial-of-Service (DDoS) attack, you know how paralyzing it can be. But the more educated and prepared you are, the less vulnerable and better off your business will be. Learn about the three main categories below:
- Volume-Based Attacks flood your website with a ton of traffic, choking out all your available bandwidth and blocking pathways.
- Protocol Attacks target the weak spots in server resources, firewalls, and load balancers.
- Application Layer Attacks, acting like normal requests, aim to crash your website.
No matter what kind of attack, early detection is critical. Here are some warning signs to look for:
- An unusually slow network performance
- Unavailability of a particular website
- Inability to access any website
- Large amounts of traffic from a single IP address or IP range
- Unusual traffic patterns like a traffic spike during what are normally off-peak times
Despite these threats to your confidentiality, integrity and availability of your business’ most critical data, knowing the signs ahead of time will put you in the driver’s seat instead of at the mercy of these growing threats. Learn more below.
How Do They Infiltrate?
Developing a sustainable strategy that works is crucial, but to do that effectively, it’s important to understand how these Distributed Denial-of-Service (DDoS) attacks infiltrate systems. See below:
- UDP Flood overwhelms the system with a deluge of User Datagram Protocol (UDP) packets.
- SYN Flood happens when the delivery of a large volume of TCP/SYN packets, often carrying a forged address, leave connections half-open and eventually overwhelm the server.
- Ping of Death causes the system to freeze or crash with malicious pings (ICMP packets) that are larger than the system can handle.
- HTTP Flood attacks a web server or application with what look like legitimate HTTP GET or POST requests.
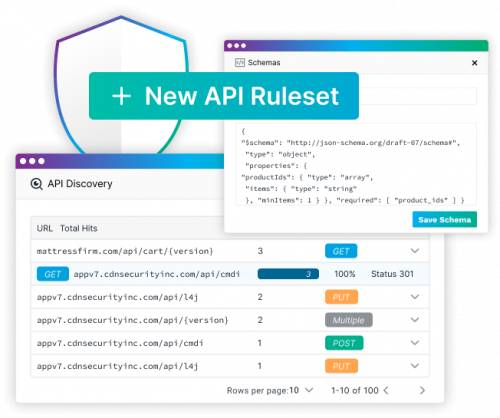
Why Investing in DDoS Protection is Vital
Much like a levee that blocks unwanted water, modern enterprise security platforms are vital to ensuring that businesses like yours are protected from an onslaught of threats caused by DDoS attacks that will severely threaten the health of your business. See below.
- Revenue Protection: Helps safeguard revenue streams while also mitigating long-term operational costs associated with upgraded infrastructure or enhanced security systems needed after an attack.
- Brand Reputation/Trust: The perception of being vulnerable to attacks takes its toll on your brand’s reputation and the trust you build with your clients and investors.
- Compliance and Security: DDoS attacks can come with legal and regulatory implications and fines associated with non-compliance.
- Cost Savings: The cost of DDoS protection is typically much lower than the cost associated with an attack.
- Time Better Spent: Focusing on DDoS mitigation and recovery efforts can divert resources from other critical IT initiatives and strategic business activities.
- Customer Experience/Retention: Attracting and retaining customers is never easy but add in a DDoS attack and it becomes a whole lot harder.
- One For All and All For One: A DDoS attack on one entity can have ripple effects, impacting partners and the supply chain.
Understanding the why enables you to make informed decisions that safeguard your online presence and establish a strategy that works now and for years to come! Take the next step with Edgio!
Implementing an Effective DDoS Strategy
An effective DDoS prevention strategy requires a multifaceted approach, combining advanced technology with expert knowledge. This is where Edge Security comes in. Learn how below:
- Adaptive Threat Monitoring: Leveraging AI and machine learning (ML) models, Edge platforms can analyze traffic patterns in real-time, identifying and adapting to new and sophisticated attack vectors.
- Predictive Analysis: These platforms can predict potential attacks by analyzing historical data and traffic trends, enabling proactive measures before an attack fully materializes.
- Anycast Network Diffusion: Edge Security can disperse traffic across multiple servers globally, diluting the impact of large attacks.
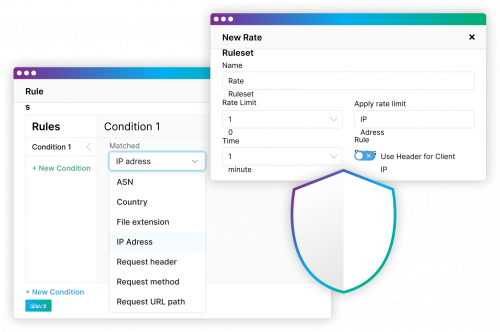
- Rate Limiting: Rate limiting prevents servers from getting overwhelmed–particularly effective against botnet-driven attacks.
- Web Application Firewalls: WAFs are essential in filtering, inspecting, and blocking malicious HTTP traffic.
- Experienced Security Staff/Monitoring: A team of seasoned cybersecurity professionals provides oversight, configures security measures tailored to specific threats, and ensures continuous monitoring and rapid response.
Shoe Carnival Discovered Unprotected Domains.
Edgio Implemented Security That Protects And Accelerates:
30 Days
Page Loads
Rate
 GigaOM Radar Edge Platform Leader & Outperformer 2024 |
GigaOM Radar Edge Platform Leader & Outperformer 2024 |