Introduction
Following the widely reported Okta breach that impacted various providers, including Cloudflare, BeyondTrust, and 1Password, we felt it was necessary to contribute to the solution by providing accessibility to more methods for sanitizing HAR files. This tool is released under an open-source license, making it available indefinitely, ensuring its utility as long as HAR files are essential for support teams.What is a HAR file?
If you’re unfamiliar with HAR files, short for HTTP Archive, they are a log of a web browser’s interactions with a website. Support teams use them to help diagnose customer experience issues. HAR files streamline a process that would otherwise be challenging and require a lot of manual effort to track down logs from different networks, devices and browsers. Widely used, a quick Google search finds about 18,700 results for support pages explaining how to create a HAR file. Every action the browser takes is captured and stored in a JSON-formatted HAR file, which captures information including complete request/response headers, content payloads, timing information (e.g. DNS lookups), and more. But as often happens in security, this convenience comes with a tradeoff. HAR files also contain very sensitive information including cookies and session tokens.What Could an Attacker do with an Unsanitized HAR file?
The short answer is a lot! A few of the potential risks associated with unauthorized access to a HAR file include:- Session Hijacking: If the HAR file contains session tokens or sensitive cookies, a malicious actor could use this information to hijack a user’s session, gaining unauthorized access to their account.
- Data Exposure: Personal information, passwords, or other sensitive data exchanged between the client and server may be exposed, providing valuable information for identity theft or other malicious activities.
- Reconnaissance: The detailed information in a HAR file can be used for reconnaissance purposes, helping attackers understand the structure and vulnerabilities of a web application. This information may aid in planning more targeted attacks, XSS attacks or other forms for injection attacks.
- Privacy Exposure: HAR files may capture a user’s browsing behavior, including visited URLs. In the wrong hands, this information could be used for privacy violations or targeted phishing attacks.
Introducing Edgio’s HAR Sanitizer

If you’re going to send a HAR file to someone (you’re having an issue with a site or app), or if you plan to receive them (you run a support team), Edgio has built a HAR sanitizer to remove all sensitive information from HAR files.
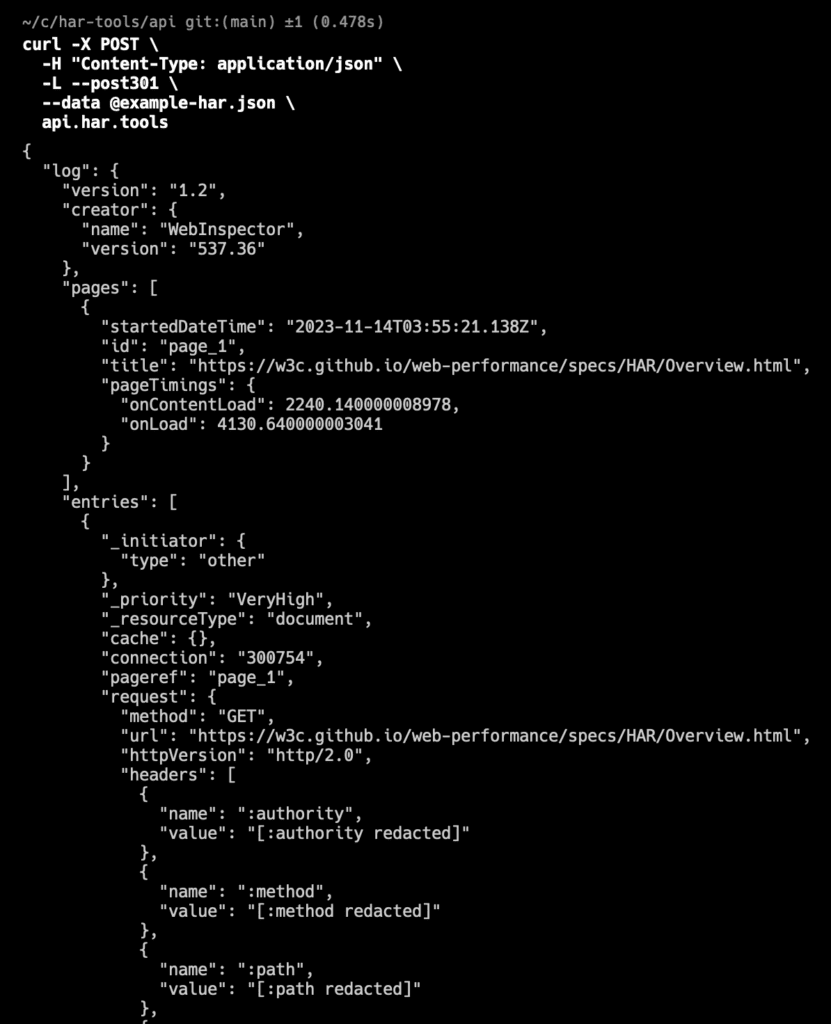
The code provides multiple deployment options to fit different use cases and workflows. You can deploy the sanitizer locally, on your own web instance, or even set up an automated workflow that sanitizes files via API. This last option works well if your support team is running ServiceNow or another workflow automation platform and receives HAR files on a regular basis.
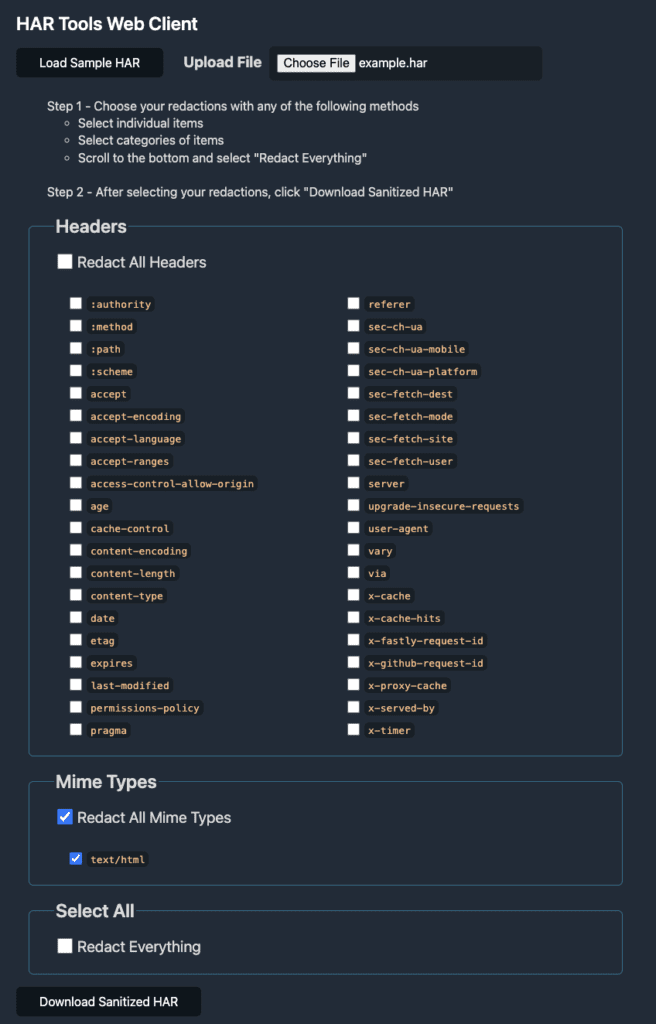
Additional Recommendations
While requiring sanitization when collecting or sending HAR files should be an essential step of any troubleshooting process, we’re assuming that many organizations are probably still sitting on old HAR files. Even if session tokens have long since expired, HAR files can contain plenty of sensitive information that bad actors would love to get their hands on. To avoid compliance issues and lower the risk of a data breach, be sure to make the deletion of HAR files part of the support process and delete any old files as soon as possible.
Conclusion
At Edgio, we’re striving to make the internet a safer place and hope you will find the tool helpful.
Powering over 4% of global internet traffic, Edgio employs proprietary technology to detect and mitigate evolving threats, including zero days. To learn more about our award-winning holistic Web Application and API Protection (WAAP), reach out to our security experts.
 GigaOM Radar Edge Platform Leader & Outperformer 2024 |
GigaOM Radar Edge Platform Leader & Outperformer 2024 | 






