By now, you’ve likely heard of a major software supply chain attack that threatens many websites using the open source polyfill.io service. This article will give you some background on the problem, as well as updated actions you can take to ensure your users are protected. While Edgio’s services are not impacted by this attack, our security team is ready to help any customers who are concerned they may have used polyfill.io in their website or application.
Background on polyfill.io
To understand the recent polyfill.io supply chain attack, we should first define the term “polyfil.” Polyfill refers to code that adds modern functionality to older browsers that lack native support for newer web features. It enables developers to deliver a consistent user experience across diverse browsers, particularly those slower to adopt the latest web standards. In the case of the polyfill.io attack, developers used polyfill to add JavaScript functionality that is not supported by older browsers.
Polyfill.io is a widely used service that automatically detects the end user’s browser and served the necessary polyfills to ensure compatibility with modern web technologies. By embedding scripts from cdn.polyfill.io (polyfill.io’s open-source CDN), developers could seamlessly provide polyfills without the hassle of manual management, simplifying the process of maintaining browser compatibility.
However, earlier this year polyfill.io was acquired by Funnull, a relatively unknown and purportedly Chinese company. It appears that the acquisition strategically marked the beginnings of a significant supply chain attack. In late June 2024, security firm Sansec warned that the service was used to inject malicious code into thousands of websites, redirecting users to scam sites and exposing them to potential data theft and unauthorized actions.
Who is Affected by the Polyfill.io Attack?
The impact of this supply chain attack is vast, affecting over 100,000 websites globally. Any website embedding scripts from cdn.polyfill.io is at risk. The malicious script introduced by Funnull redirected users to scam sites, enabled data theft, and potentially allowed remote code execution. Notably, this attack also compromised mobile users and specifically targeted devices at particular times, evading detection by security tools and analytics.
The Supply Chain Attack: What You Need to Know
While there are many nefarious possibilities that attackers might take after compromising third-party scripts, the more common ones include:
- Redirection to Malicious Sites: Websites using compromised scripts can unknowingly redirect users to scam sites, like fake Google Analytics or sports betting sites. These malicious redirects compromise user trust and can lead to phishing attacks.
- Data Theft and Code Execution: The modified script can steal sensitive data from users and perform unauthorized code execution, posing severe risks to website integrity and user privacy. Unauthorized scripts can exfiltrate sensitive user data, such as personal information, credit card details, and login credentials, to external servers.
- Cross-Site Scripting (XSS): Malicious scripts can execute in the context of the user’s browser, leading to session hijacking, malware distribution, and as previously mentioned, data exfiltration.
- Site Defacement: Attackers can modify the appearance or content of a web page, leading to brand damage and loss of user trust.
- Performance Degradation: Malicious or unauthorized scripts can cause significant application performance issues, slowing down websites and providing poor user experiences.
What Can You Do to Protect Your Site and Users?
Considering this attack and the high reliance on third-party libraries in today’s modern apps, developers and site administrators must take immediate action to protect their websites and users. Here’s our latest guidance:
- Identify Sites Using Polyfill.io: The first step to protecting your site and users from this attack is to know whether your code references polyfill.io.
If you have a Static Application Security Testing (SAST) solution, you could run a query to look for references to polyfill.io (syntax may vary, but the following Regex gives you the idea):
result = Find_Strings().FindByRegex(@\”https?://(cdn.polyfill.io)\”);
Additionally, Static Code Analysis (SCA) tools, which focus on identifying and managing open-source components and their vulnerabilities, can help. SCA tools maintain databases of known vulnerabilities associated with libraries and frameworks. By scanning your codebase, SCA tools can flag any dependencies (including polyfill.io) with known security issues.
If you don’t have SAST or SCA in place, we recommend following these steps from ZAP, an actively maintained GitHub Top 1000 project dedicated to security testing.
docker run -t zaproxy/zap-stable zap.sh -cmd -addoninstall pscanrulesBeta -zapit https://www.example.com/
The one-line command used by ZAP’s Polyfill.io Script Detection to check for scripts being served from the polyfill.io domain (requires Docker); for a more robust scan, run a ZAP baseline scan.
- Implement Client-Side Protection: Client-Side Protection helps safeguard against supply chain attacks by monitoring and controlling scripts and third-party API calls in real time, preventing the loading of malicious code and blocking unauthorized interactions with malicious hosts.
Edgio’s Client-Side Protection solution allows teams to implement a positive security model by only allowing defined third-party scripts from executing in client browsers.
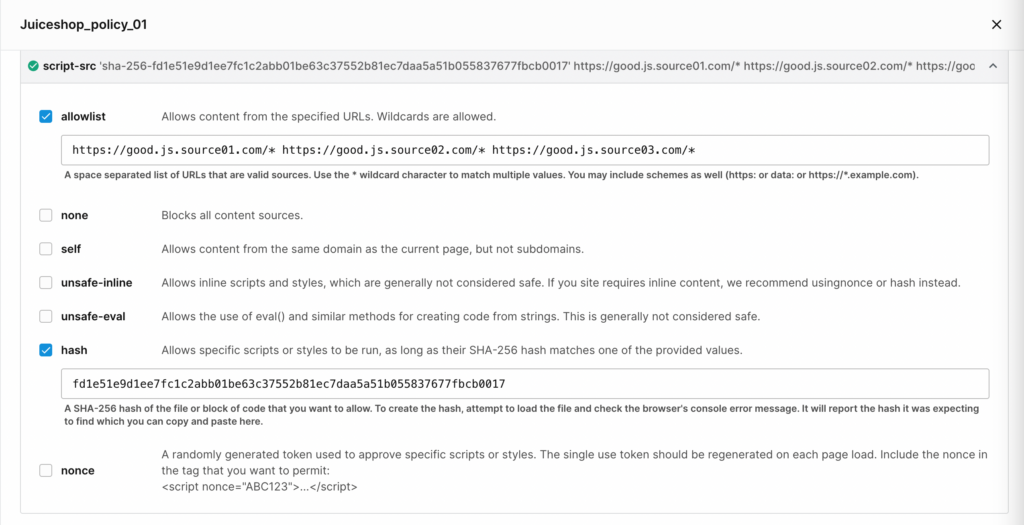
Example of a Client-Side Protection policy. A positive security model can be applied by directing which script sources can be called in the allowlist.
- Remove Polyfill.io Scripts: Remove any references to cdn.polyfill.io from your code. Replace them with alternative, trusted sources for polyfills or discontinue the use of polyfills altogether, as modern browsers rarely require them.
Edgio’s Edge Functions can also be used to dynamically rewrite any polyfill references made by your site to any safe URL (available in our GitHub repo here). This additional security layer can be thought of as a simple and easy to deploy “virtual patch,” giving valuable protection and buying time for your dev teams to go back and remove and replace references to the compromised library.
- Monitor for Compromises: Regularly check your website for signs of compromise, such as unauthorized redirects or data exfiltration. Implement security monitoring tools to detect unusual activity and keep up to date with security advisories and updates related to the libraries and services you use.
- Switch to Trusted Services: If your use case requires polyfills, look for alternative services from organizations with a proven track record. However, you know what they say about guarantees in life- so it’s important to use the controls and best practices stated above to lower risk. After all, developers will use what they think works – polyfill.io was quite a popular service – and not all have a secure coding background.
Conclusion
The Polyfill.io supply chain attack serves as a stark reminder of the vulnerabilities inherent in third-party software components. At Edgio, we emphasize the importance of securing your web applications through robust multi-layer security. Our Web Application and API Protection (WAAP) service, which includes Client-Side Protection to detect and block malicious scripts running on client-side browsers, ensures continuous protection against supply chain attacks and other evolving threats.
Additionally, our new Attack Surface Management (ASM) solution provides comprehensive visibility across your entire web-facing footprint, allowing you to identify and mitigate vulnerabilities proactively, safeguarding against potential exploits before they can be leveraged by attackers.
Lastly, Edgio’s Managed Security Services also stands ready to help implement, or fully manage your web application security. With 24/7 security operations, a dedicated threat intelligence team, and assigned security architects, you can rest assured that you web assets are continually monitored and protected against the latest threats, allowing your teams to focus on innovation while we handle your security needs.
If you have any questions or need assistance protecting your websites from supply chain attacks, feel free to reach out to Edgio’s Security experts.
 GigaOM Radar Edge Platform Leader & Outperformer 2024 |
GigaOM Radar Edge Platform Leader & Outperformer 2024 | 






