By: Tom Gorup & Andrew Johnson
You’ve probably noticed the frequency of cyberattacks in headlines has grown drastically since the Israel/Hamas war began. We’ve seen a hike in everything from site defacement to DDoS attacks to data exfiltration from hacktivists all over the world. There have been no borders nor boundaries they aren’t willing to cross.
While more noteworthy attacks on highly public sites like the Jerusalem Post make news headlines, an interesting trend we’ve noticed is one-to-many site defacements on less visible targets. What we mean by ‘one-to-many’ are attacks targeting a single resource to compromise many websites. Many of the attacks we’ve seen, who are claiming to be tied to Middle East conflict interests, sit behind single IPs, which led us to hypothesize that many of these threat actors (TA) are gaining access to a single vulnerable resource or application that allows them to manipulate any site sitting behind that proxy or on that server. The majority of attacks we’ve seen that follow this pattern have taken advantage of hosting providers. We consider these opportunistic attacks and consequently take no one off the list of potential targets, the Internet is their target.
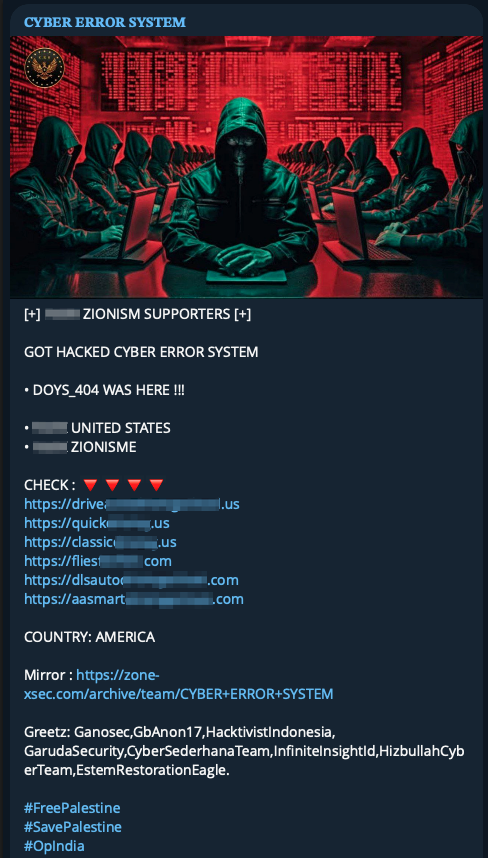
Over the last two weeks, we’ve been analyzing publicly announced site defacements across hacker forums, and what we found was a little unexpected and certainly interesting. For example, of the 4,069 site defacement attacks reported by hacktivists over the last two weeks, we found 3,480 unique domains targeted, but limited to only 1,426 unique IP addresses. Going one step further, we found only about 271 unique ASN’s (Autonomous System Numbers) associated with the same target list.
These stats speak volumes to the types of targets these hacktivists are going after. If you’re still wondering if your own site is at risk…well it is! You might think that less heavily trafficked sites are too small to get caught up in this war, but the reality is that attackers are taking every opportunity they can get to post their flag on someone’s site in the name of hacktivism. While we cannot speak to every individual TA’s motives, it’s likely most have some desire to gain creditability and stimulate pride as they post to a room full of individuals waiting to celebrate their successes. Let’s walk through a few examples to illustrate our hypothesis.
Threat Actor: SanRei
In this example, let’s look at a TA that goes by the name SanRei. This individual targeted 69 unique domains across 23 unique IP addresses and 15 ASN’s. Seventy-two percent of SanRei’s targets sit within a single hosting provider’s ASN.

Furthermore, after analyzing nine domains, we found several of the sites contained the same text/copy, but with different graphics, page layouts, and themes. The sites certainly seem related. Whether the TA created and controlled the sites, that they later defaced and bragged about in a Telegram channel, is hard to prove, but it certainly is a strong possibility.
Websites with very similar content, hosted on the same IP, later claimed to be defaced by SanRai.
Threat Actor: ./BRILLIANT
Next examining the work of a TA that goes by the name ./BRILLIANT, we find this individual targeted 1,112 unique domains across 229 unique IP addresses and 61 ASN’s. Seventy percent of ./BRILLIANT targeted domains are within the Universitas Gadjah Mada’s ASN. It seems likely that ./BRILLIANT found a vulnerability within a single app that hosts a number of individual blogs on *.web.ugm.ac.id.
At face value, ./BRILLIANT looks like they compromised 700+ websites, but the likely reality is they popped one and leveraged that access to manipulate many individual blogs. Quite the successful one-to-many compromise.
Threat Actor: AnonCyber504_ID
These hacktivists haven’t just targeted fake websites and blogs, legitimate business websites are in their list of targets as well. Threat actor AnonCyber504_ID targeted 60 unique domains across 37 unique IP addresses and 16 ASN’s. Forty-six percent of AnonCyber504’s targets sit within one hosting provider’s ASN, and many appear to belong to legitimate businesses.

While none of the defaced sites we examined belong to a Fortune 500 company, the point here is that hacktivists and other TA’s seem to be targeting sites indiscriminately, whether large or small, government or private enterprise.
Conclusion
We’re sure you’ve heard of most of these before, but what can one do to protect their website from one-to-many hacktivist attacks?
Multi-factor Authentication
Are you tired of seeing this on the list of recommendations yet? There’s a saying, “when you are tired of saying it, people are starting to hear it.” In that case, make sure you have MFA enforced on all accounts with access to your web resources and admin panels.
Endpoint Protection
We know you might have that endpoint protection rollout project that stalled out six months ago. Spin it back up, it’s time to make it a priority. That can go a long way in reducing your security workload down the road.
Patch Management
Patching is a thankless task and runs on forever, but it is extremely necessary. How do you think these one-to-many attacks are taking place? Take the time to build a good program, you’ll thank yourself in the long run.
Web Application and API Protection
As we mentioned before, patching is hard, but when you leverage a good Web Application Firewall (WAF), especially a cloud-delivered one with built-in DDoS protection, API security, and bot management, you’ll be able to breathe easier knowing you can stay protected between the time a vulnerability is discovered and a patch is rolled out, with capabilities like virtual patching.
Protect All of Your Sites
While most mature organizations have a lot of these safeguards in place, the recent activities carried out by hacktivists underscore the importance of protecting all your web assets, not just your “crown jewel” sites.
User Education
This phrase creates so much nausea, yet we think it’s completely underrated. It wouldn’t surprise us if a majority of these one-to-many compromises started with a phishing attack. Take the time to make sure your team understands why all these security controls are necessary. The key here is to make sure it’s timely, relevant, and engaging. Having trouble making it engaging? Reach out; our team has a ton of ideas to help out.

To learn more about Edgio’s award-winning Web Application and API Protection (WAAP) solution, contact one of our security experts, today.
 GigaOM Radar Edge Platform Leader & Outperformer 2024 |
GigaOM Radar Edge Platform Leader & Outperformer 2024 |